The Latest Fortinet News
Product and Solution Information, Press Releases, Announcements
| Enabling Security in 5G Private Networks | |
| Posted: Mon Dec 14, 2020 01:42:36 PM | |
|
As business, technology and networks evolve, so must the infrastructures that support them, opening the door for 5G to show its true worth. The key difference between 5G and its predecessors is that 5G opens up a multitude of opportunities for value-added services at the enterprise level, compared to more consumer-based models used in 4G and earlier. Because of this, many companies are looking to create their own private 5G platformsa move that comes with new cybersecurity considerations and risks. A 5G Critical Use Case Emerges in Private NetworksMany businesses have viewed 4G networks just as a mobility play because there was less opportunity for building services on top of mobile connectivity. But 5G changes this perspective. It has the capability to address business segment needs and use cases beyond connectivity in addition to the consumer segment. This intersection of a platform to drive business and consumers is one of the big promises with 5G. A trend of building enterprise-level 5G private networks is already emerging across industries, such as manufacturing, logistics, Oil and Gas with early rollouts taking place. In fact, according to ABI Research, spending on 5G private and shared enterprise networks could surpass spending on public mobile networks in 15 years. Indeed, because most businesses do not have the capability to set up their own 5G network in-house, MNOs, then, need a strategy and service offerings for private 5G mobile networks moving forward. Security Needs in 5G Private NetworksAccording to Ronen Shpirer, Director of Communication Service Provider Solutions Marketing at Fortinet, many businesses assume that having a private network keeps them safe. But this is not often the case. Going wireless can increase the attack surface due to factors such as increased Industrial Internet of Things (IIoT) exposure, physical mobility of devices on the network, and interplay between the enterprise, MNO, IoT manufacturers, operational technology (OT) vendors, and suppliers. As these 5G private networks are built, they become a vital part of an enterprises infrastructure and critical to daily operations, making security that much more important. A strong layer of security is something that is definitely crucial, says Shpirer. The entire enterprise, at least the productive part of the enterprise, might be relying on that non-public mobile network. Because of the nature of 5G networks, security must be handled in a two-part approach: First, public network availability and integrity must be maintained, similar to the standard security needs of a 4G network. Second, value-added security services are needed to protect data ecosystems that are enabled by the 5G capabilities and ecosystem. Fortinets goal is to deliver a common security platform that provides a unique solution for the complete protection of 5G infrastructure as well as data ecosystems across multiple different possible private network architectures. Fortinet Security Solutions in 5G Private NetworksThe primary components of a 5G network are the Radio Access Network (RAN), the 5G cores Control and User Planes (CP and UP), and Multi-access Edge Compute (MEC). According to Shpirer, key areas of cybersecurity to address in such a network are as follows:
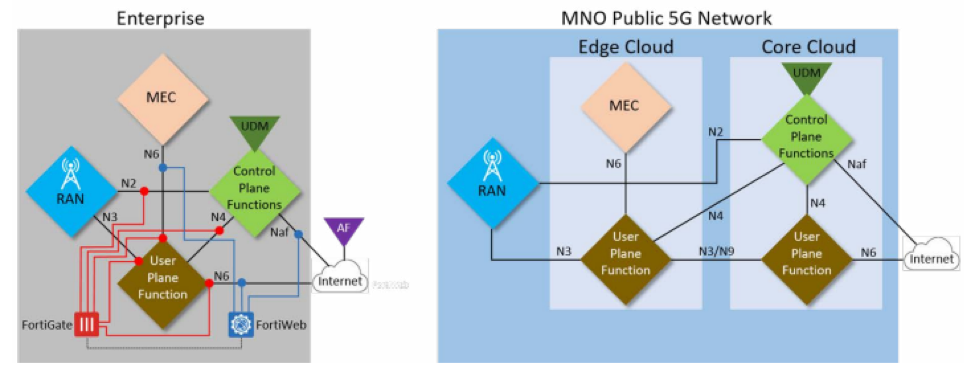
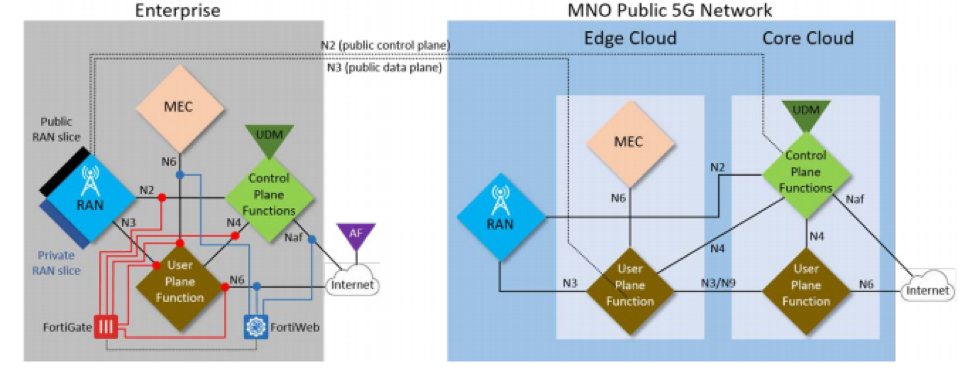
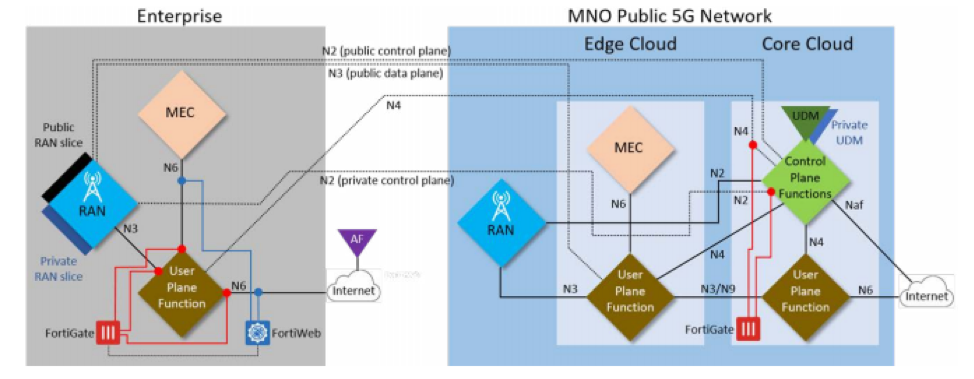
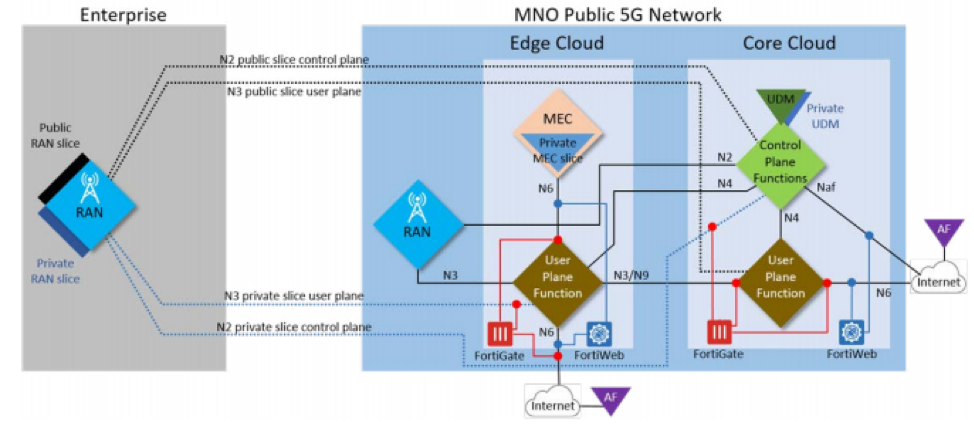
Fortinet solutions that address these risks include FortiGate for RAN to core and PDN security and FortiWeb for API and application-level security. These solutions can also be used to provide revenue-generating managed security services to the customer, on top of the 5G private network. Existing FortiGate firewalls can protect the customer environment from external PDN threats, and FortiGate can also provide specific OT and IIoT security, as well as segmentation to limit potential threat propagation. FortiWeb can be used to provide internal API and application security. In general, the Fortinet Security Fabric allows for the inclusion of additional capabilities, maximizing adaptability and integration. Because we have the Fortinet Security Fabric, says Shpirer, I can have, for example, endpoint visibility and control that is already integrated with the FortiGate. Just add something else and you can provide visibility, device control, and microsegmentation per device to your customers. Fortinet Cybersecurity Implementation for Multiple Private Networks ArchitecturesSecurity implementation also depends on network architecture. One architectural option for a private 5G network is to create an MNO-independent network in which all four components are physically isolated from public 5G. The other option is to create an MNO-dependent network in which some or all of the components may be on the public 5G network but are logically isolated. The former is often more secure, but the latter is often more cost-effective. The customization, agility, control, and complexity profiles of each architecture differ when viewed from an enterprise perspective vs. from an MNO perspective. For enterprises, the MNO-independent solution maximizes the metrics, while for MNO, a full public sharing option does the same. How Fortinet Security Solutions Integrate Into Each of These Architectures:
Fortinet: A Strong Player in 5G Private Network SecurityWith the right security solutions in place across the spectrum of private 5G network architectures, MNOs can offer clients secure and flexible solutions for building value-added services on a 5G platform. When industries and verticals adopt 5G to drive innovation, automation, efficiency and safety, a strong security foundation delivered as part of the private 5G network will ensure that these benefits are safeguarded. |