
Fortinet Managed IPS Rules for AWS Network Firewall
Filter malicious traffic and enhance network security on Amazon VPCs
Security Simplified for Amazon VPCs
Enterprises are speeding digital transformation, making the cloud’s role in delivery of services more important than ever. Securing virtual private cloud networks and application workloads is critical, and must not add to a security team’s operational burden.
Fortinet Managed IPS Rules enhances the baseline protection offered by AWS Network Firewall. It reduces the learning curve and delivers network security that is effective, available, and scalable-while keeping management simple.
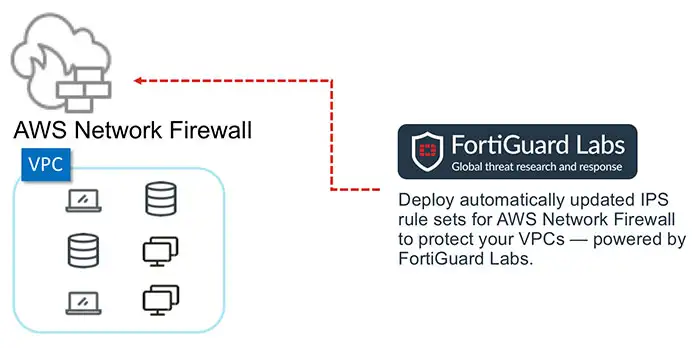
Improve Security While Reducing Resource Needs
Protect VPCs and workloads from security breaches
IPS rules are automatically updated by FortiGuard Labs to address the constantly evolving threat landscape. Our threat research experts analyze 100B+ events every day from millions of security sensors deployed globally.
Significantly reduce security management and operations overhead
Fortinet Managed IPS Rules are set up to address the most common vulnerabilities out of the box. A security expert is not needed for deployment and management.
Provide rapid on-demand protection for business-critical workloads in AWS VPCs
Fortinet Managed IPS Rules is available in the AWS Marketplace for rapid deployment anytime. It protects workloads across VPCs and accounts.
Streamline operational costs without sacrificing security
Avoid upfront investments by leveraging pay-as-you-go (PAYG) pricing models and fully-managed infrastructure. Align network security costs with your usage.
Watch how Managed IPS Rules protects your application workloads and VPCs
Fortinet Managed Intrusion Prevention System (IPS) Rules, powered by FortiGuard Labs, provides broad coverage to protect against common network vulnerabilities. With millions of global network sensors, FortiGuard Labs monitors the worldwide attack surface and employs artificial intelligence (AI) to mine that data for new threats. These rules can be deployed in just a few clicks with no infrastructure to manage, significantly reducing complexity of your cloud operations.
Types of Enhanced Protection
![]()
Server and OS
Rules that detect vulnerabilities targeting operating systems and common server applications, including DNS, email, and remote access
![]()
Malware Detection
Rules that detect communication attempts from malware backdoors, worms, and remote access Trojans (RATs), including command and control traffic
![]()
Application, Network, and IoT
Rules that detect attempts to exploit vulnerabilities in common client applications, including desktop software, network, and IoT
![]()
Web Client
Rules that detect exploits targeting vulnerabilities in web browsers, including Chrome, Firefox, Internet Explorer, and Edge.
![]()
Web Server
Rules that detect exploits targeting web server vulnerabilities, including both web servers (e.g., Apache) and proxy web servers (e.g., Squid)
![]()
Web Application
Rules that detect exploits targeting vulnerabilities in common web applications, including popular CMS platforms such as WordPress and Joomla

