The Latest Fortinet News
Product and Solution Information, Press Releases, Announcements
| How Attackers are Targeting SMBs During COVID-19 | |
| Posted: Thu May 28, 2020 11:40:08 AM | |
|
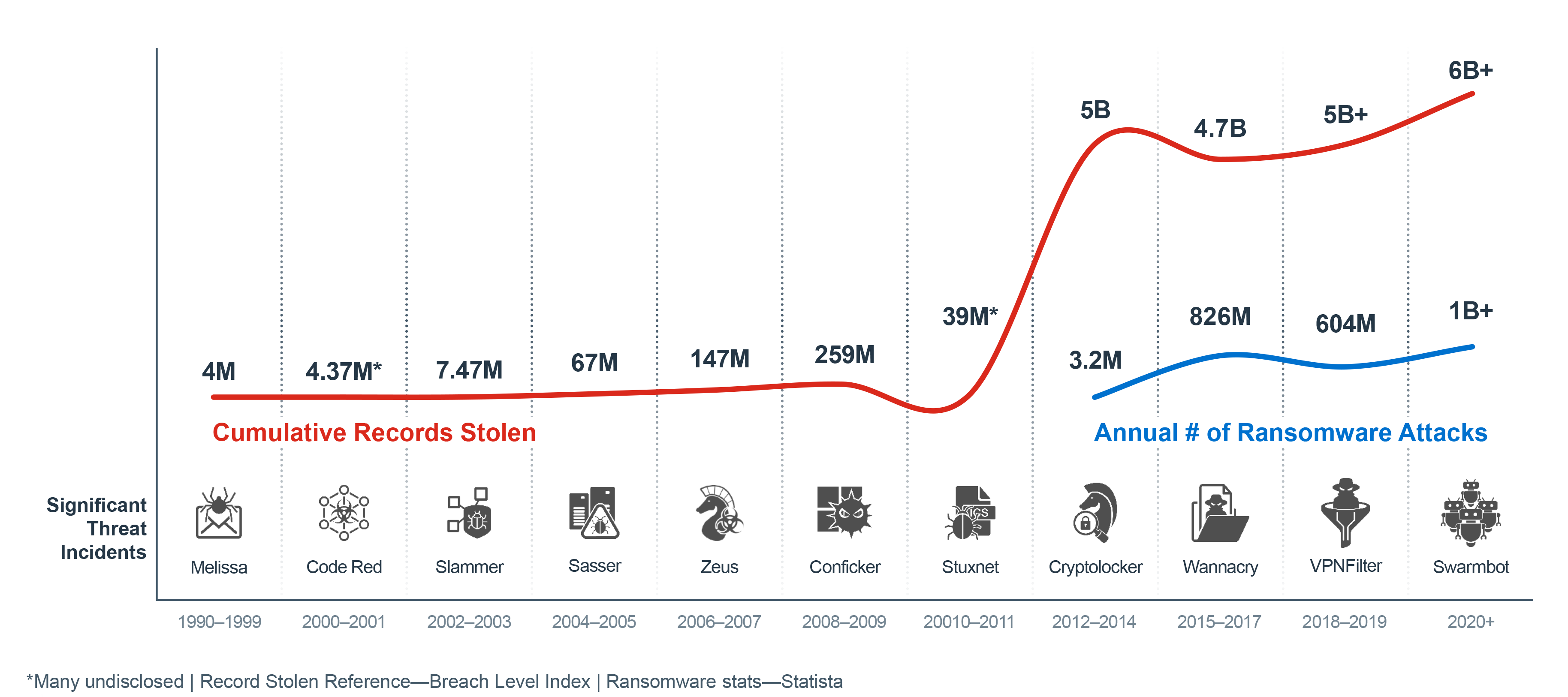
With 71% of ransomware attacks targeting small-to-medium sized businesses (SMBs), it continues to be the prevailing form of malware used by attackers to disrupt organizations. The rapid adoption of new digital innovations often introduces new security gaps and makes it easier for attacks to spread across the flat and open internal network. For many, the loss of critical business cycles and revenues from systems that have ground to a halt far outweighs the price of the ransom itself. The Fortinet Security Fabric provides comprehensive network security and advanced threat-intelligence sharing to help SMBs detect and protect against ransomware attacks.
Advanced Threats Continue to AdaptEven advanced threats still rely heavily on social engineering
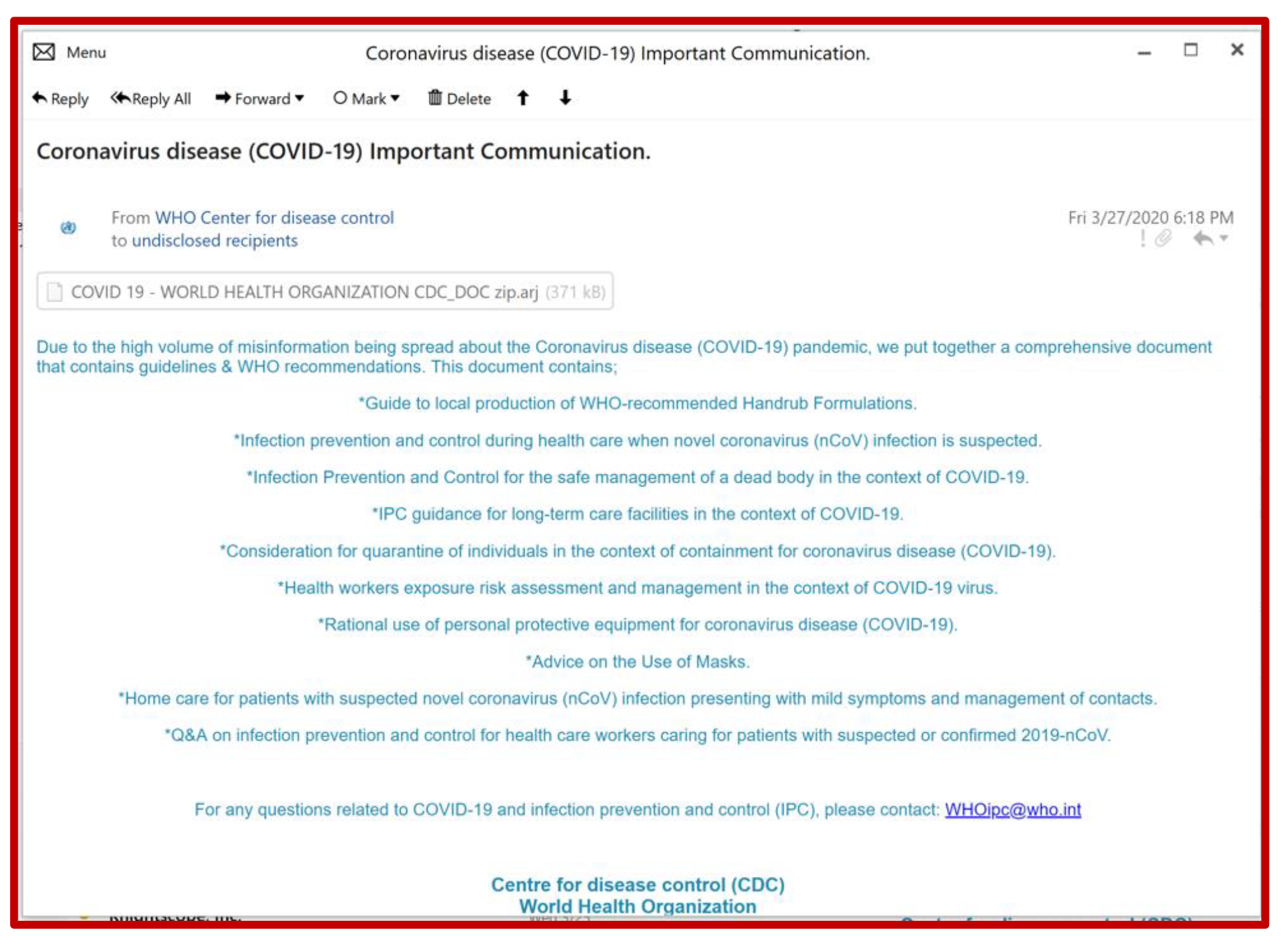
Coronavirus disease (COVID-19) Important Communication.
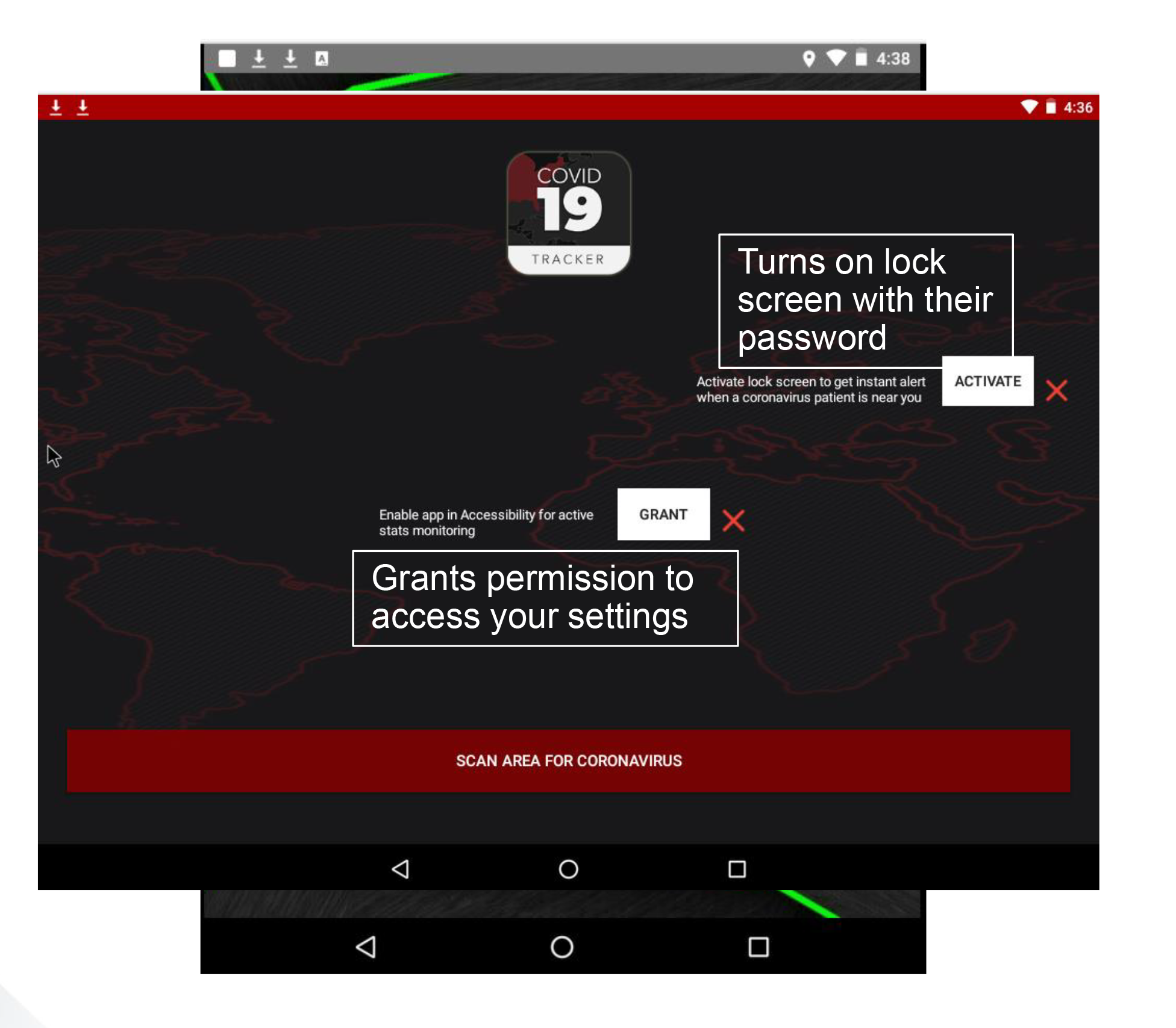
Due to the high volume of misinformation being spread we put together a comprehensive document that contains guidelines & WHO recommendations. CovidLock
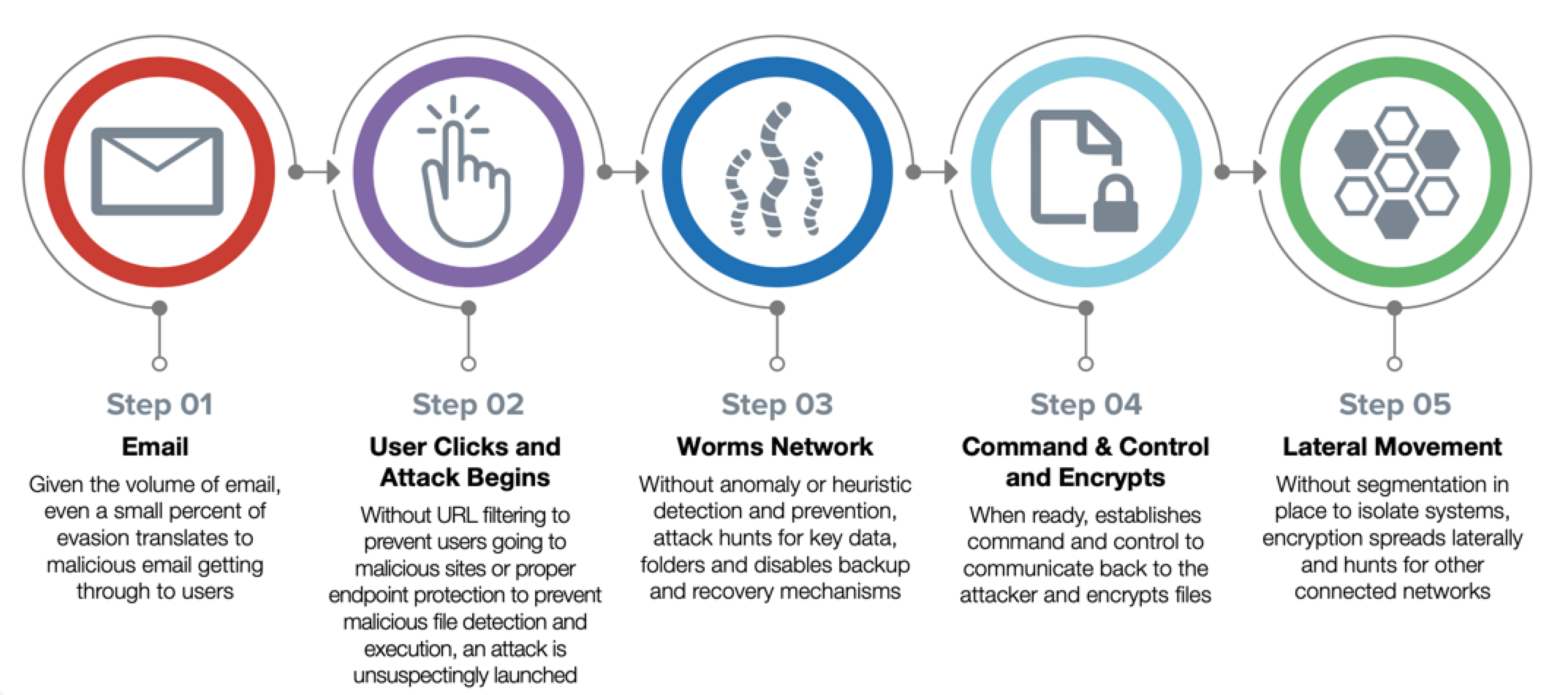
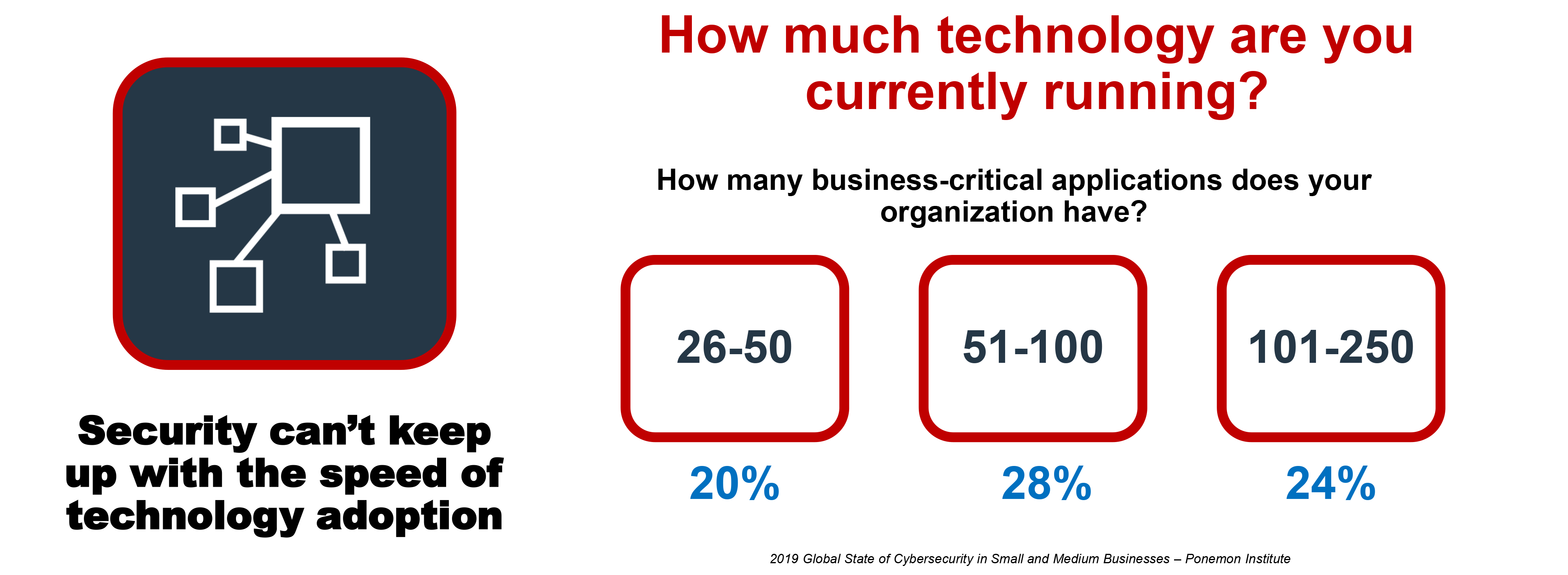
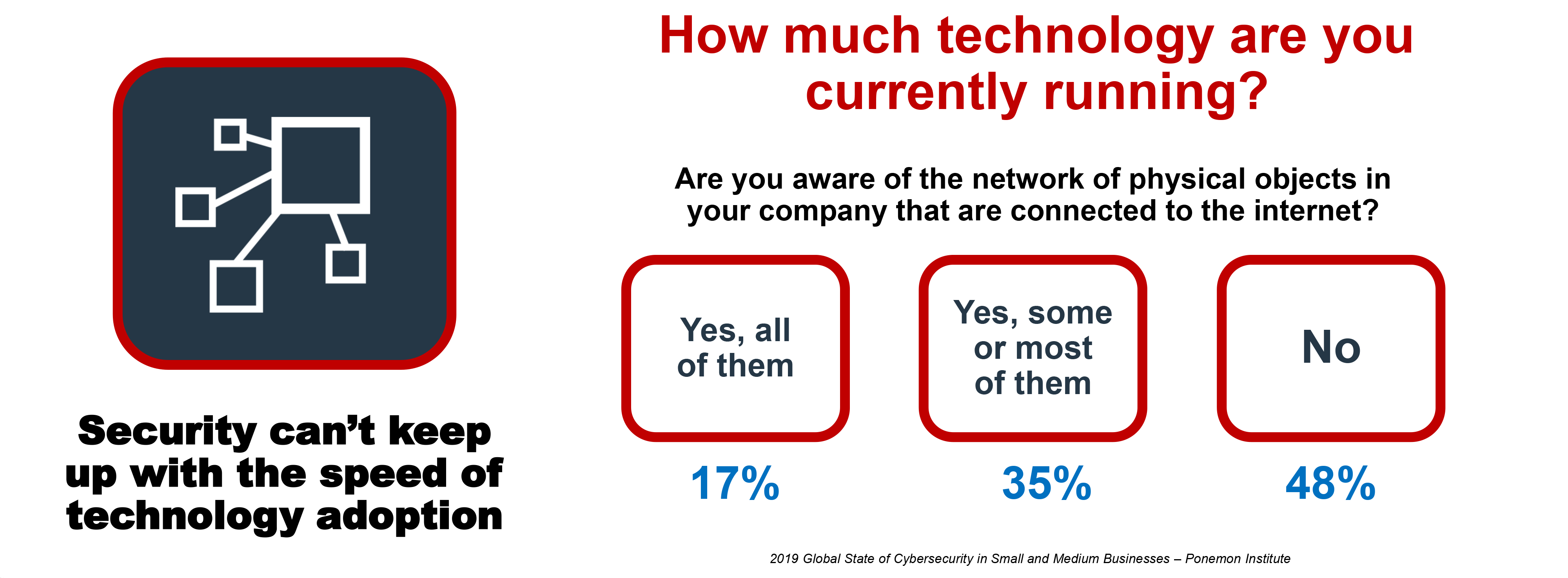
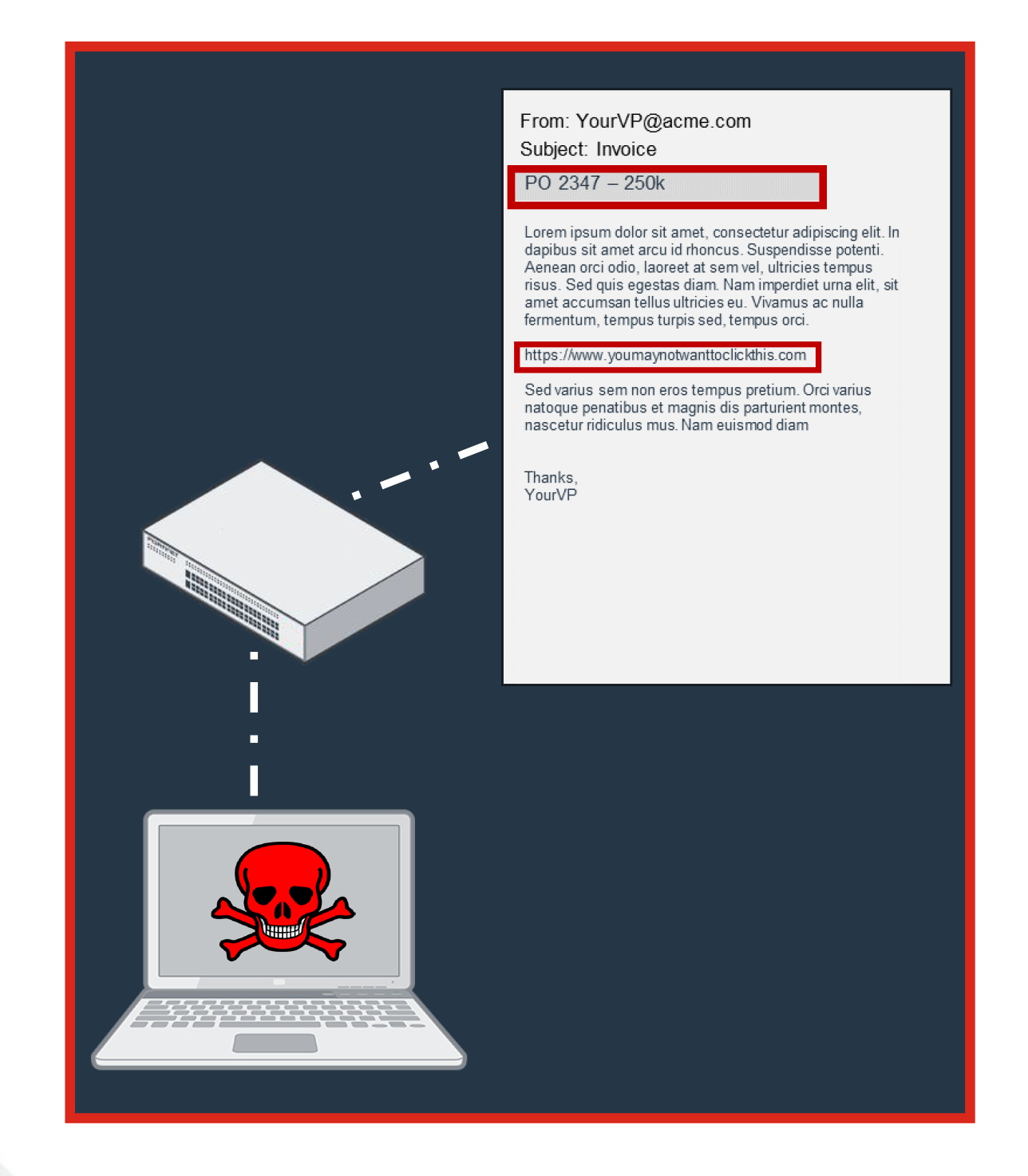
SMB Ransomware TrendsHow Ransomware Gets InThe pressing need for speed and agility across businesss of all sizes has led to the rapid adoption of innovations (e.g., cloud-based tools, Software-as-a-Service [Saas], smart devices) that bring convenience along with complexityquickly creating vulnerabilities and making it easier for even basic threats to get past outdated defenses at various points of entry. Ransomware-as-a-Service (RaaS) that enables attackers to merely invest in an attack carried out by others and the natural IT knowledge of younger generations have made it easier for low-level hackers to easily blast a wide target base and expose one of those holes and is one reason that has led to such high rates of SMBs being hit with ransomware. Email Vulnerabilities Email is the primary way that ransomware gets inside a businesss network. Many users still unintentionally open a malicious attachment or URL that slips by consumer-grade email filters. More often these days, attackers rely on social engineering and business email compromise (BEC) scams where users unknowingly give attackers the information they seek to set off a series of eventslike getting the victims phone number and replicating known sites to obtain user credentials. For SMBs that often rely on consumer-based email solutions that lack advanced email security checks, recognizing threats and avoiding social engineering schemes rely on a users individual judgment to identify the threat and avoid infection. Was It Only Ransomware?If ransomware was introduced into the network, then attackers gained access. While ransomware may have been the primary motive, other nefarious toolssuch as monitoring software, command-and-control (C&C) code, or assimilation into botnetsmay have also been introduced to launch additional attacks or siphon data at a later date. Therefore, any ransomware-compromised business must do further investigation into logs and systems for full and effective remediation. How Does Ransomware Typically Work?
SMBs By the Numbers
Why the Numbers?
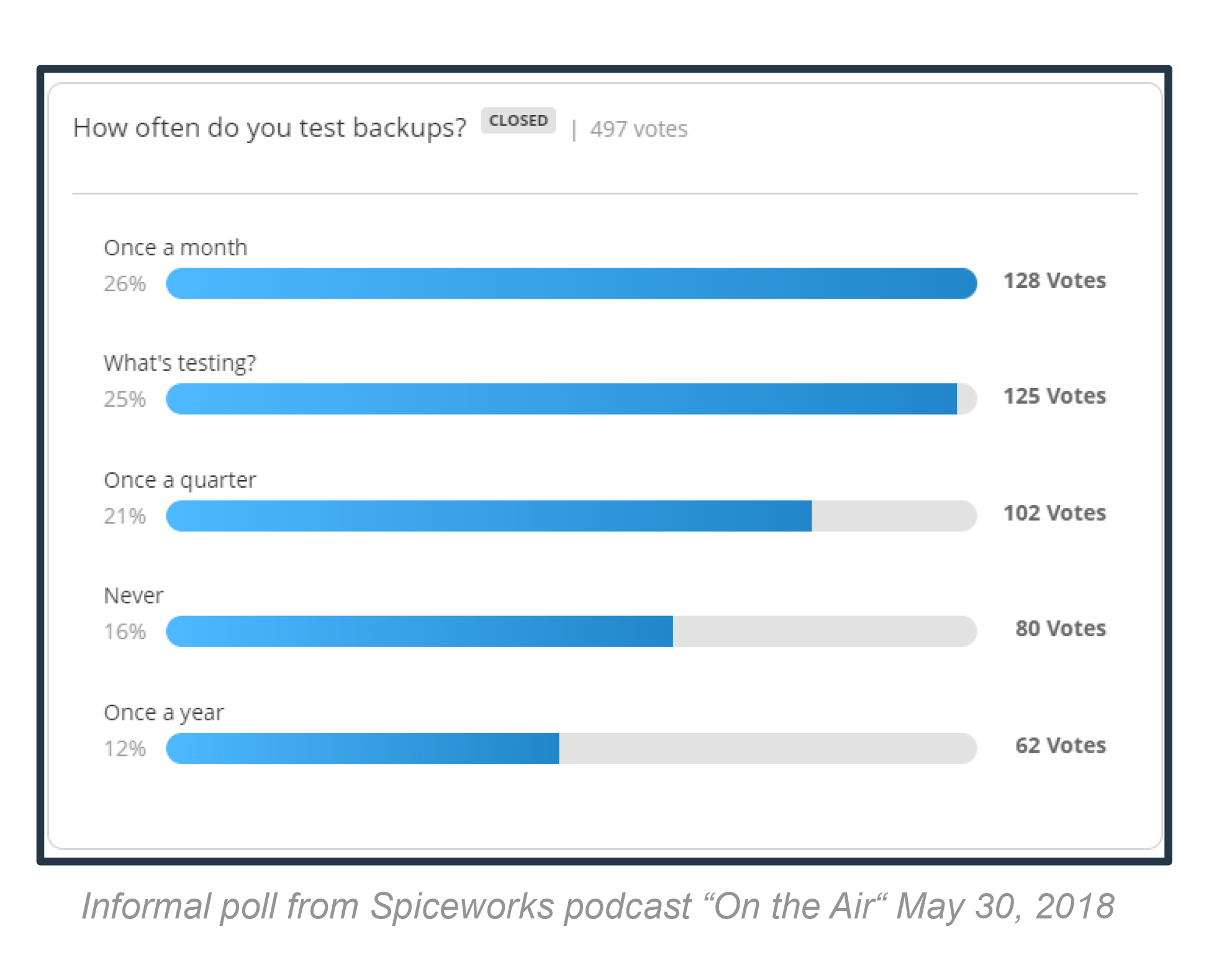
We Rely on Backup and RecoverySingle point of failure ok?
A Successful Approach to SMB Security Must Be...
How Ransomware Avoids Traditional SMB SecurityHow Fortinet Can Help The Fortinet Security Fabric enables organizations to stop known and unknown ransomware across their environment through automated sharing of actionable intelligence. Most Common Ways Ransomware Enters
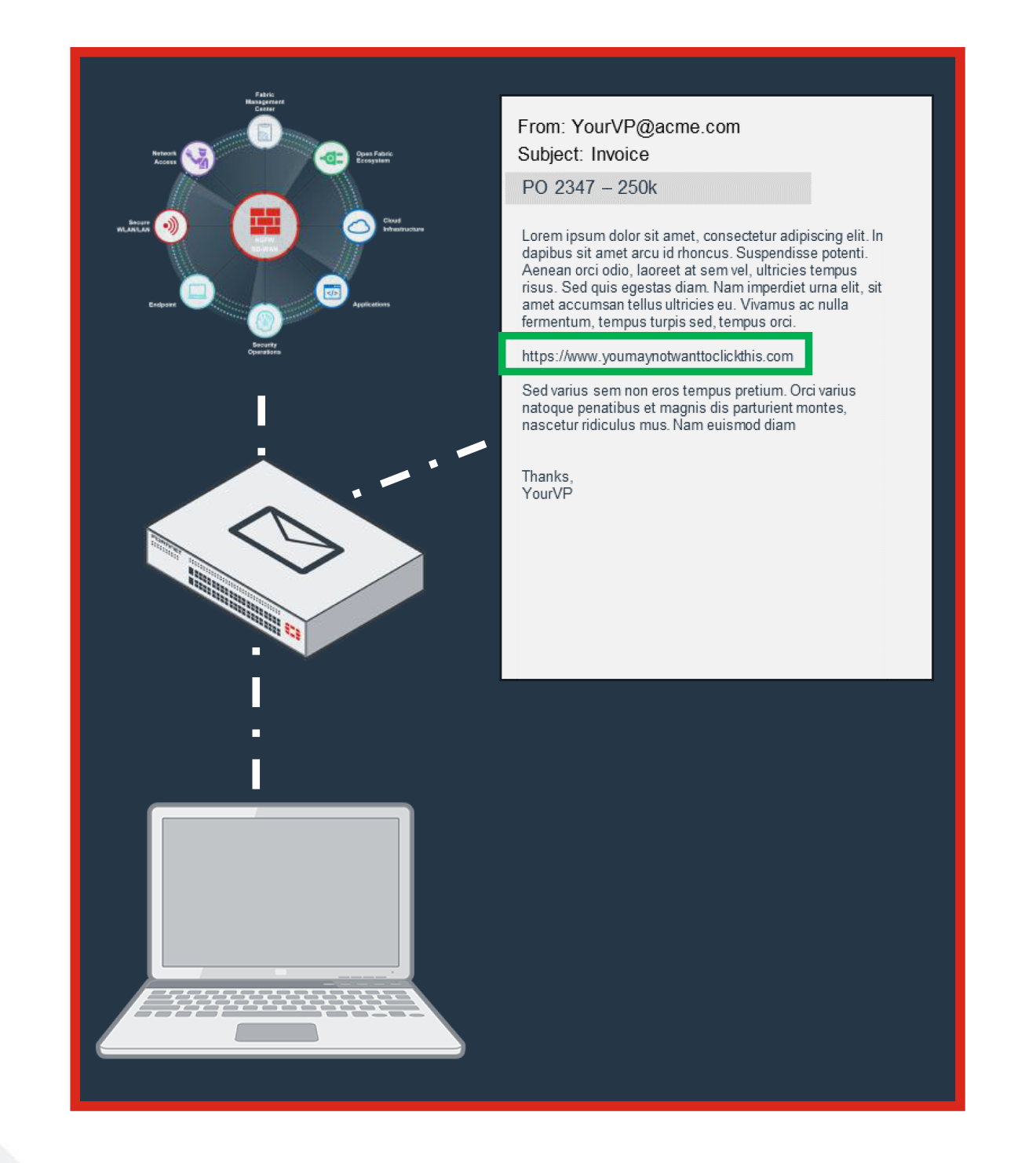
How Malicious Emails Circumvent SecurityMalicious Attachments
Inadequate analysis of attachment
No ability to decrypt and analyze
Designed to evade
Designed to specifically evade O365 Email Vulnerabilities Email is the primary way that ransomware gets inside a businesss network. Many users still unintentionally open a malicious attachment or URL that slips by consumer-grade email filters. More often these days, attackers rely on social engineering and business email compromise (BEC) scams where users unknowingly give attackers the information they seek to set off a series of eventslike getting the victims phone number and replicating known sites to obtain user credentials. For SMBs that often rely on consumer-based email solutions that lack advanced email security checks, recognizing threats and avoiding social engineering schemes rely on a users individual judgment to identify the threat and avoid infection. How Malicious Emails Circumvent SecurityMalicious URLs Embedded in Email
Inadequate analysis on target website
Can't analyze embedded links
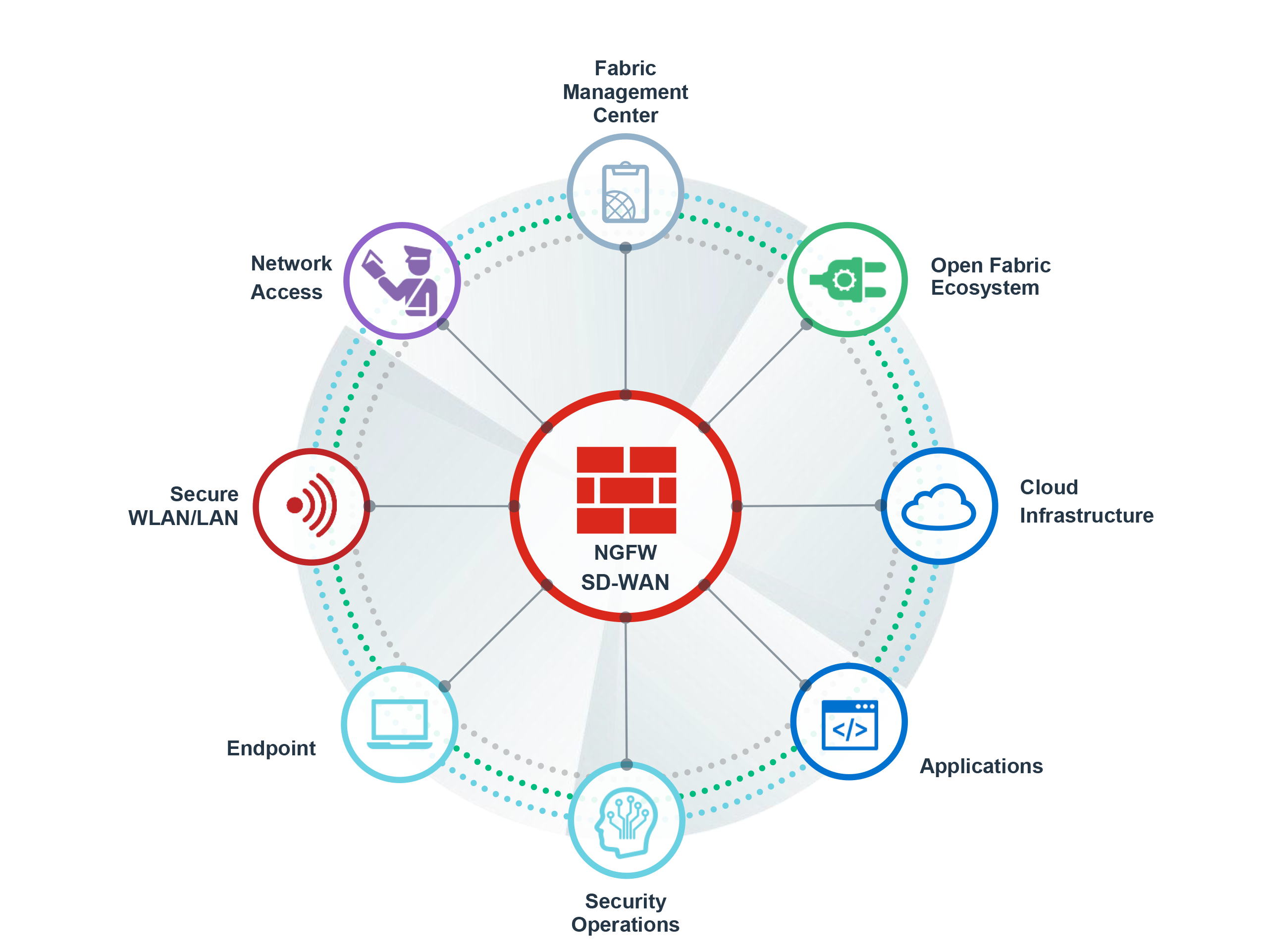
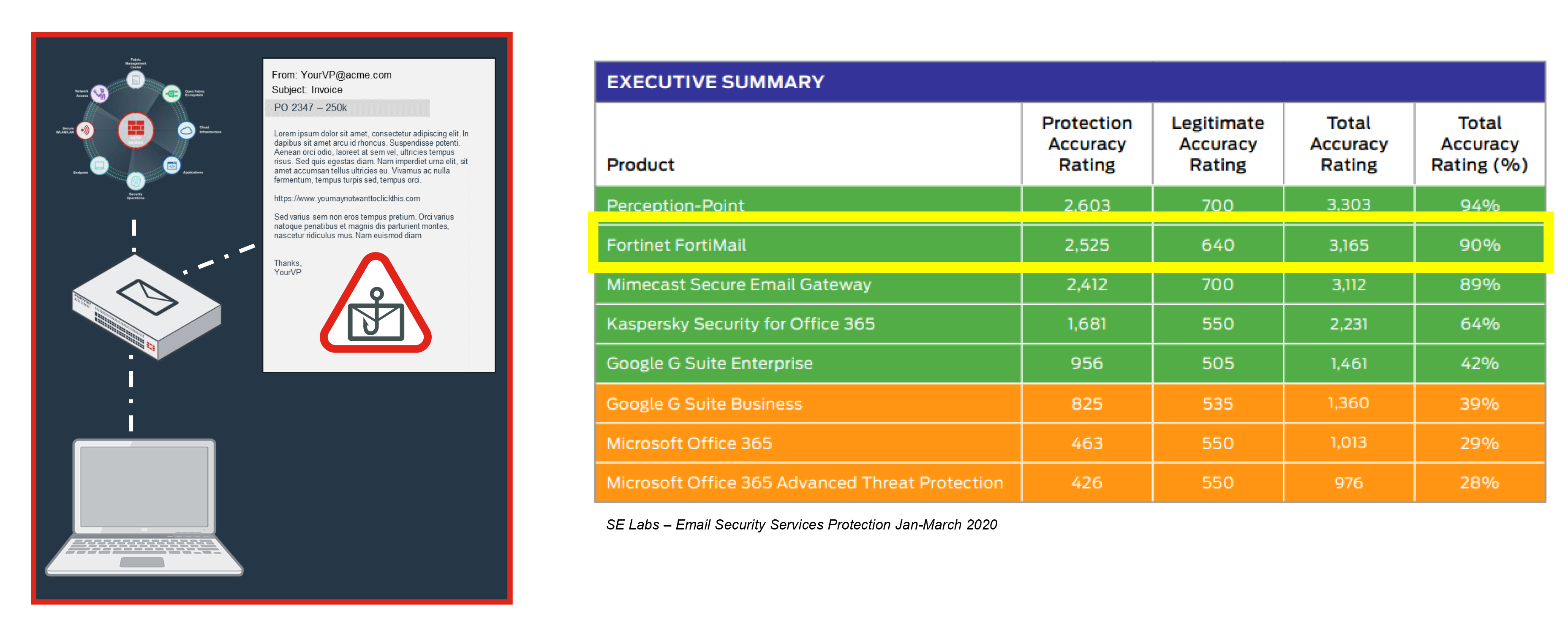
Fortinet Email SecurityThe FortiMail family of appliances is a proven, powerful messaging security platform for any size organization, from small businesses to carriers, service providers, and large enterprises. Purpose-built for the most demanding messaging systems, the FortiMail appliances utilize Fortinet's years of experience in protecting networks against spam, malware, and other message-borne threats. Fortinet Security FabricBroad visibility of the entire digital attack surface to better manage risk Integrated solution that reduces the complexity of supporting multiple point products Automated workflows to increase speed of operations and response
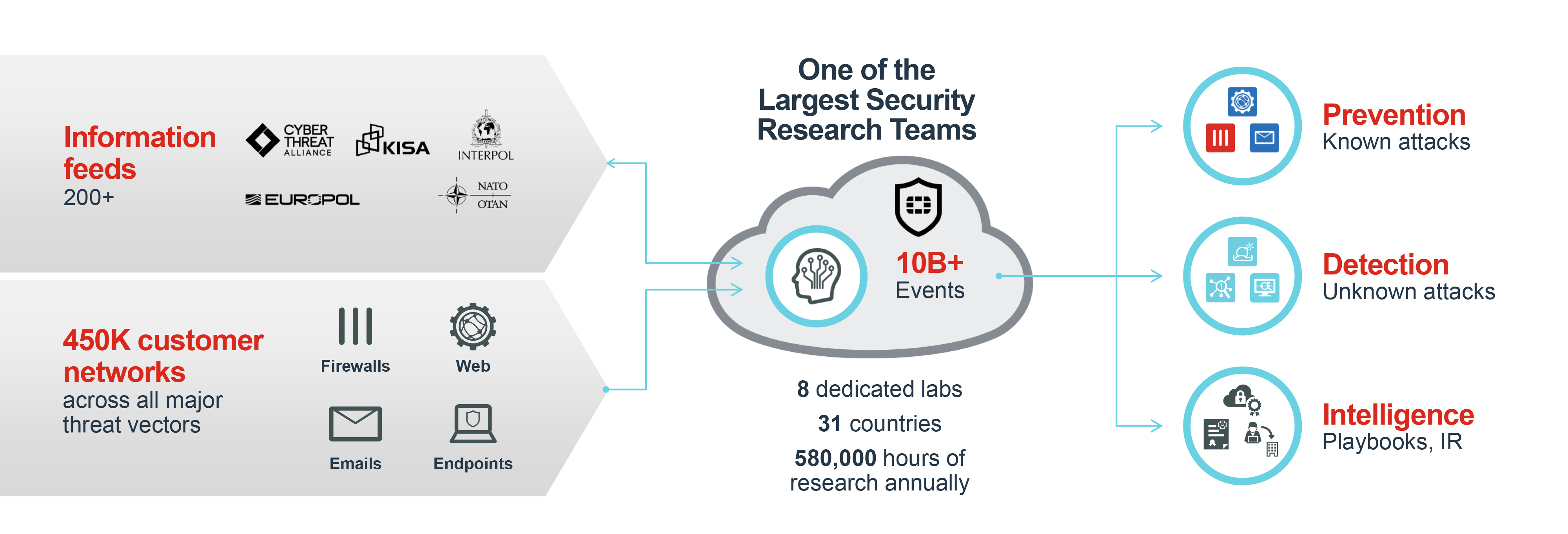
FortiGuard Labs AI-Driven IntelligenceBillions of events analyzed every day
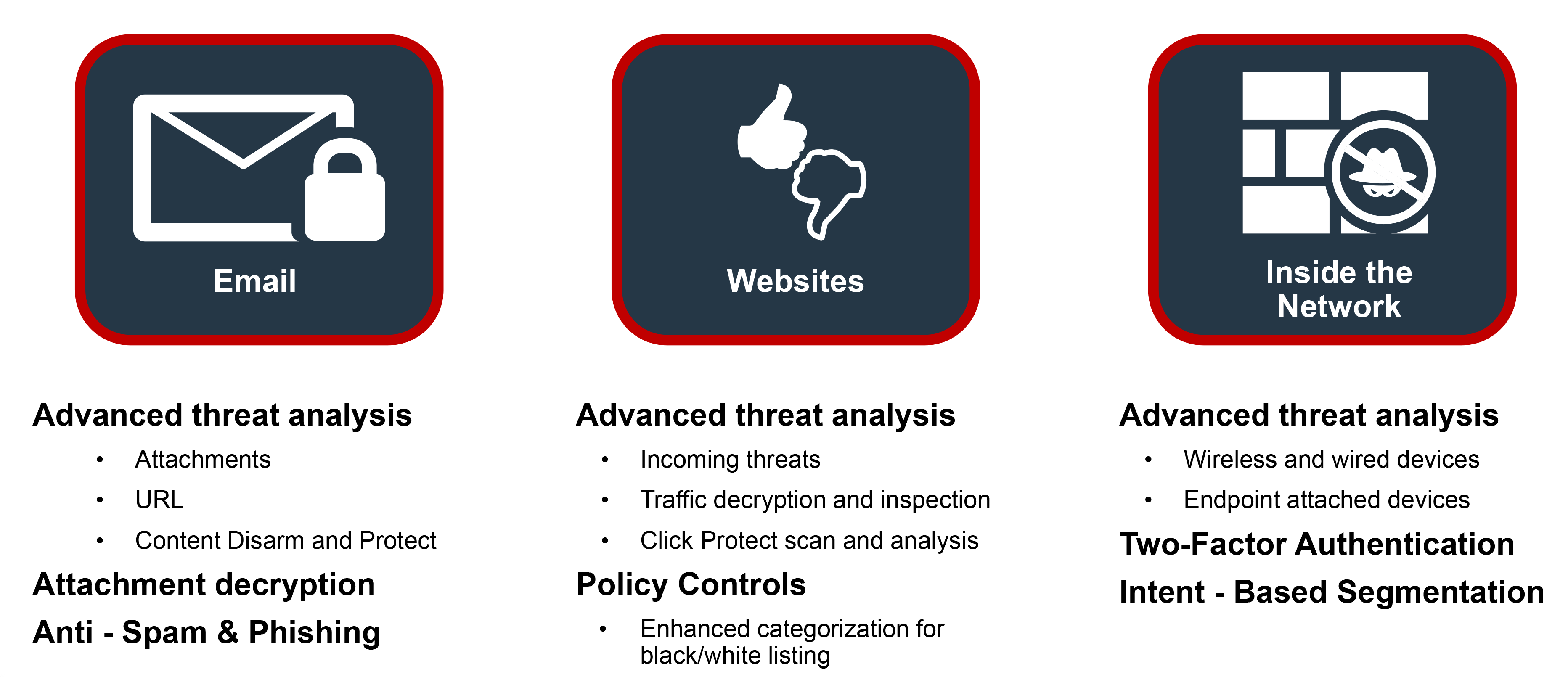
How Fortinet Secures EmailMalicious Attachments
Advanced analysis of known and unknowns
Decrypts and analyzes
Content Disarm and Reconstruct
How Fortinet Secures EmailMalicious URLs Embedded in Email
Advanced threat analysis on target website
Analysis of embedded links
How Fortinet Secures EmailPhishing
Common Network Security LimitationsHow Malicious Sites Circumvent SecurityDrive by Downloads
Limited policy controls to control browsing
Inadequate analysis on incoming traffic
No firewall in place or VPN unused
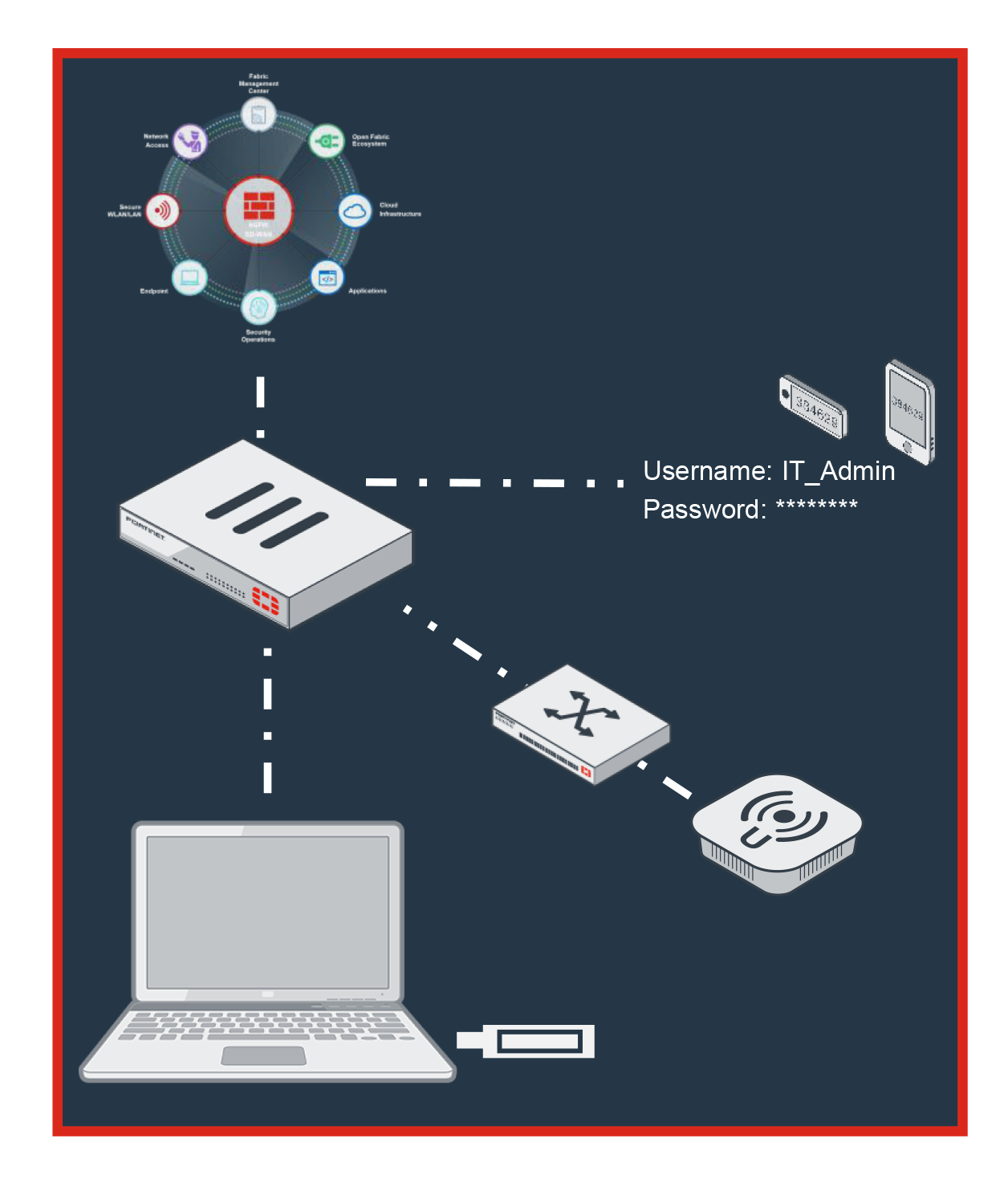
How Attackers Circumvent Network SecurityAvoiding the Firewall
No threat analysis on traffic from wireless or wired devices
Inadequate analysis on attached devices
No multi-factor authentication to block stolen credentials
Fortinet Security Driven Networking
Fortinet AI Driven Security
How Malicious Sites Circumvent SecurityDrive by Downloads
Enhanced policy controls to control browsing
Advanced analysis of unknowns
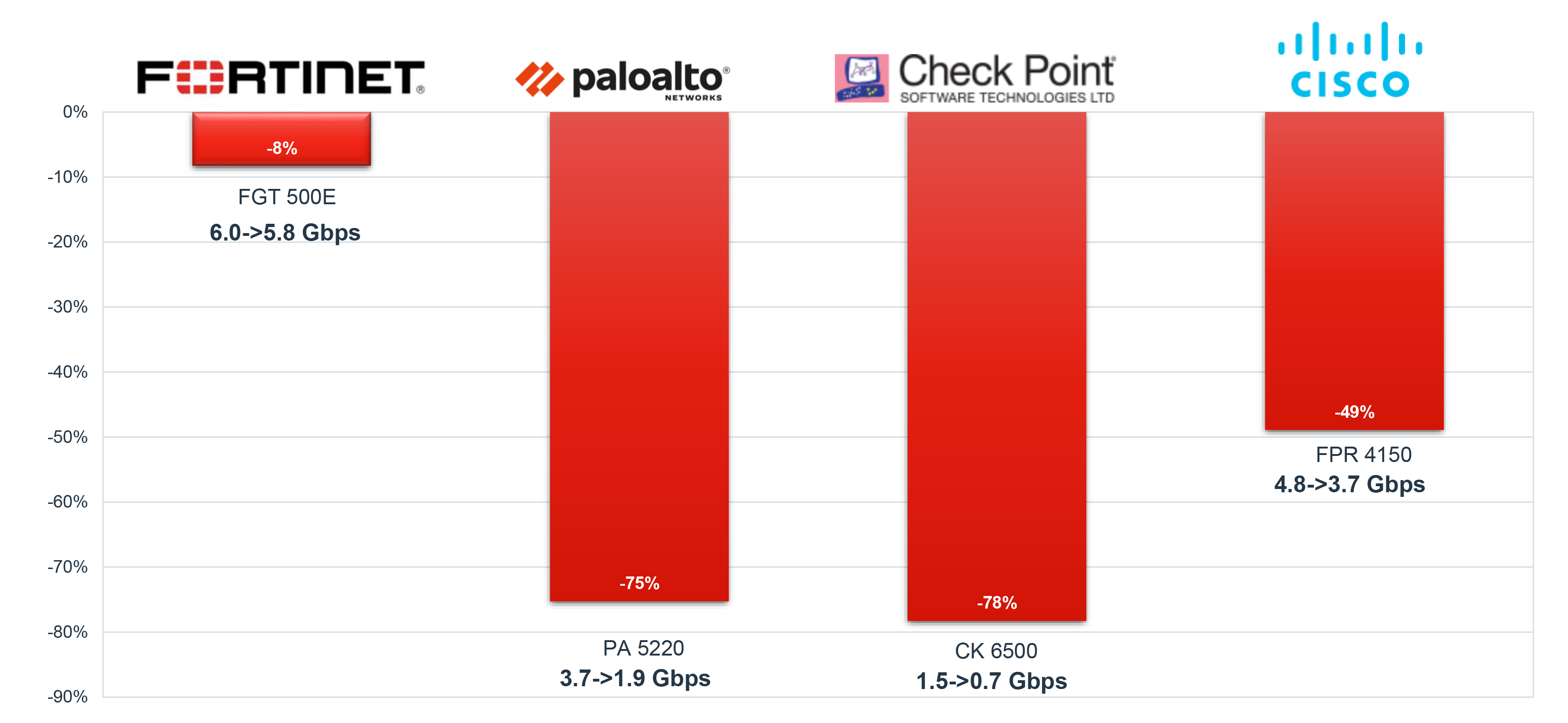
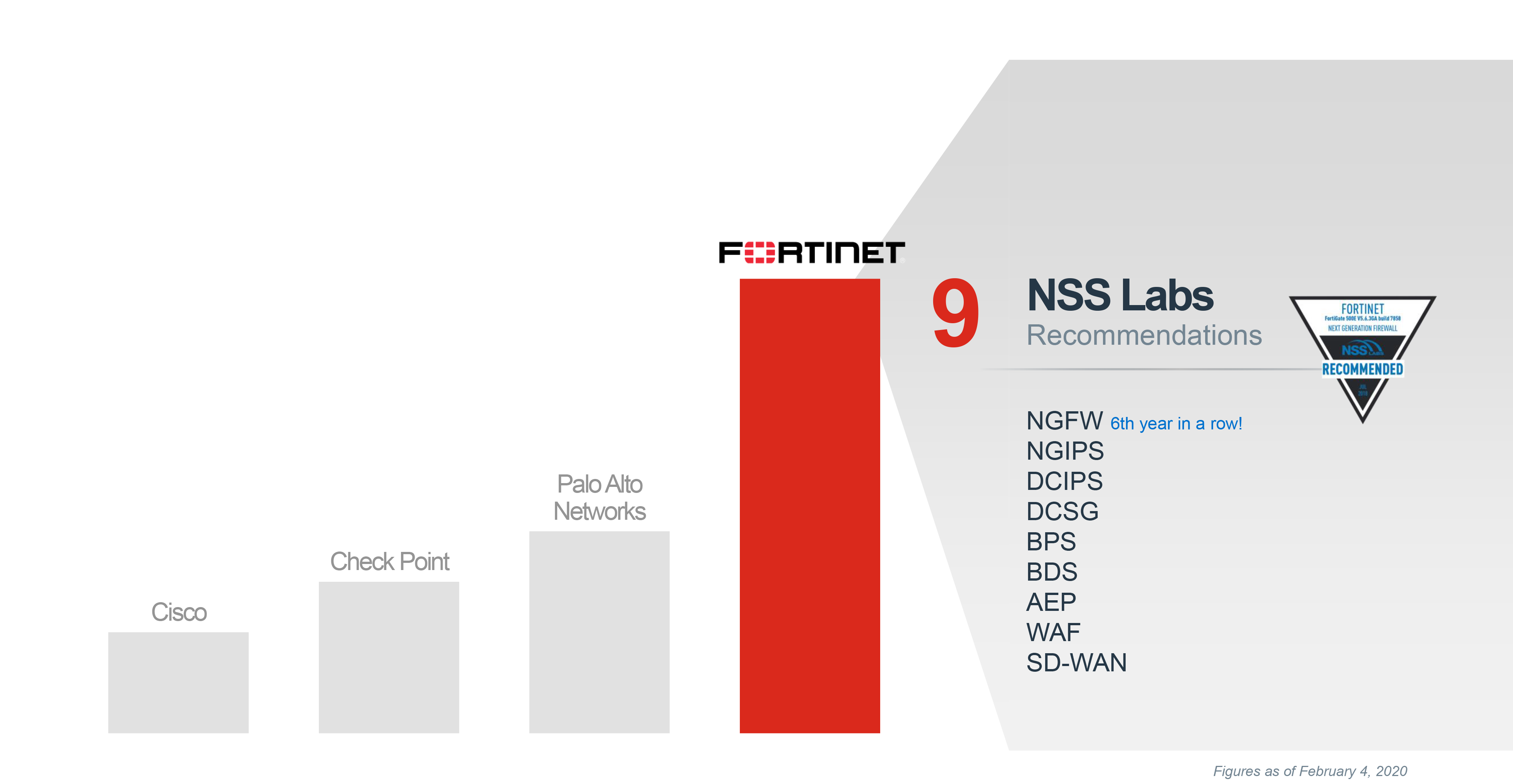
Fortinet Superior SSL PerformanceNSS Labs NGFW 2019 New SSL Performance Test
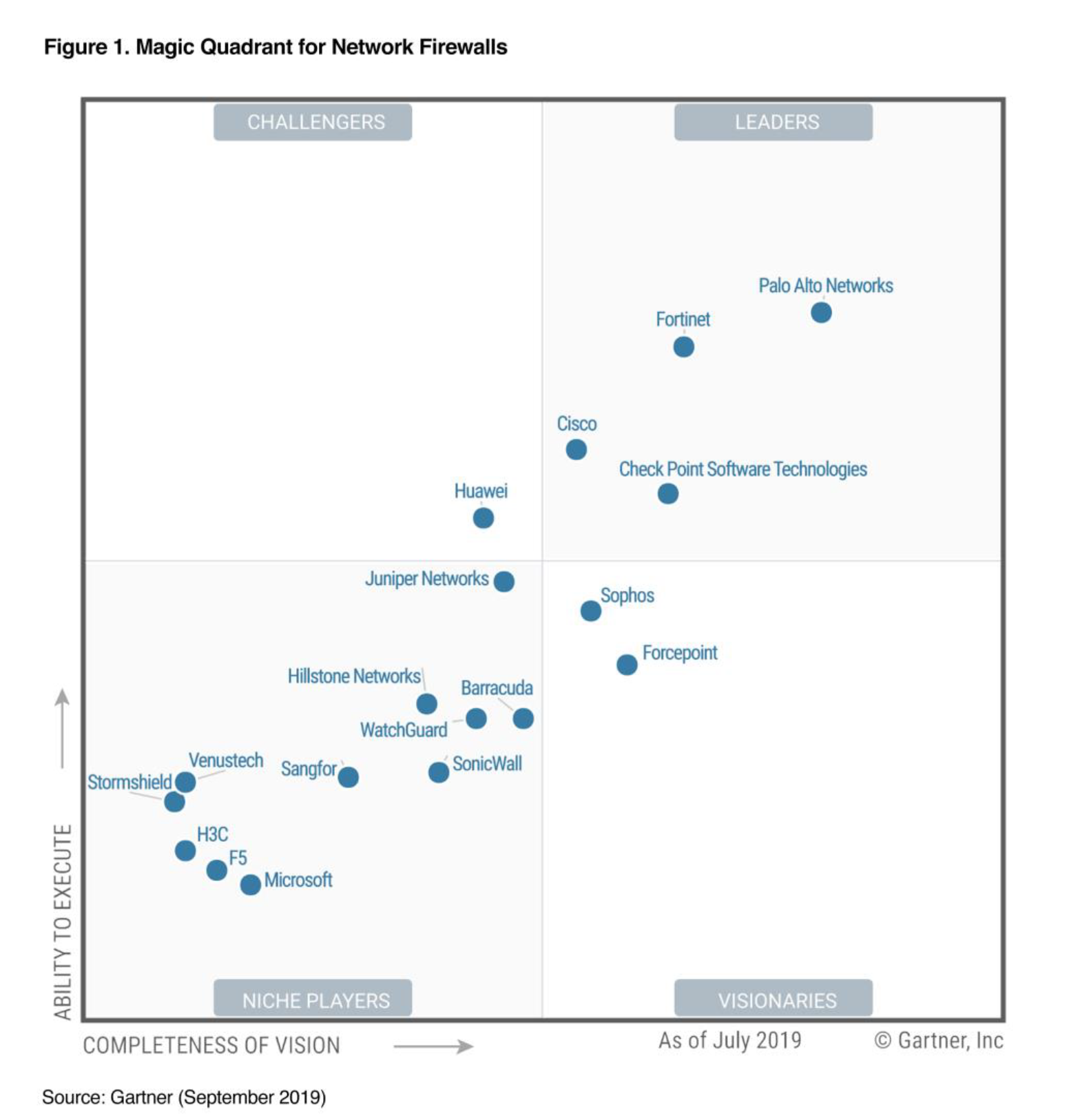
Gartners 2019 Magic Quadrant for Network Firewalls
Fortinet Recognized as a Leader in this Magic QuadrantMarks 10th time in a row that Fortinet is in the Magic Quadrant for Network Firewalls Gartner Magic Quadrant for Network Firewall, Rajpreet Kaur , Adam Hills,, Jeremy DHoinne , John Watts, 17, September 2019. This report was previously titled the Magic Quadrant for Enterprise Networks Firewalls. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Fortinet Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose How the Fortinet Security Fabric Protects YouAvoiding the Firewall
Security extended to wireless and wired devices
Advanced analysis of unknowns on endpoint
Two Factor Authentication (2FA)
Fortinet Protects Across Your Environment
NSS Labs 3rd Party CertificationsMost recent test results
|